Identity-Based Cryptography: A Certificate-Free Paradigm
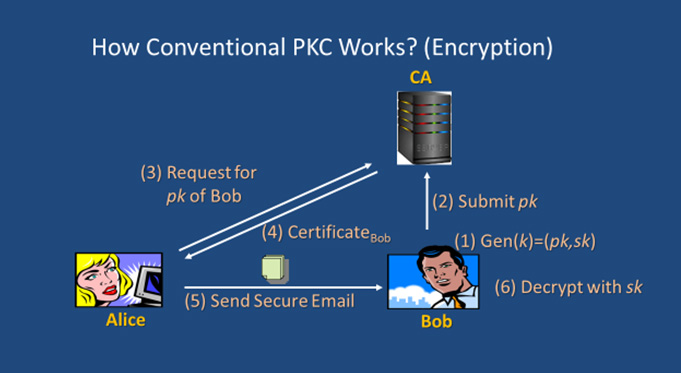
In public key infrastructure (PKI), a digital certificate or public key certificate is an electronic certificate that binds an entity which can be a person or an organisation to its public key. The user public keys and the corresponding certificates are managed by a Certification Authority (CA). The certificate management will become inefficient when the database grows large. The concept of identity-based (ID-based) cryptography, a certificate-free paradigm that solves the certificate management issue, was put forth by Shamir in 1984. The first practical ID-based encryption scheme based on bilinear pairings was due to Boneh and Franklin in 2001. Many ID-based schemes have been proposed since then.
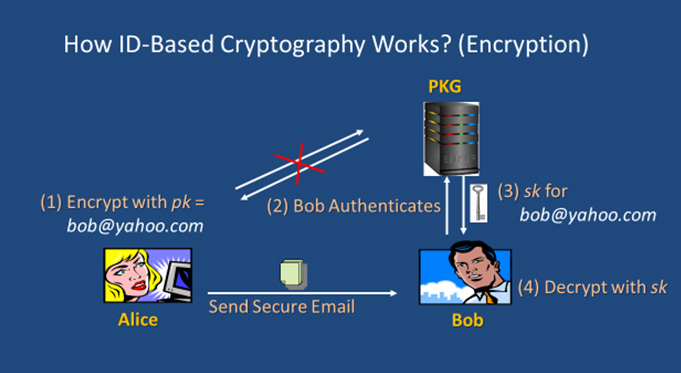
In ID-based schemes, users need exchange neither private keys nor public keys. Generally, an ID-based scheme is an asymmetric or public key cryptographic scheme wherein the public key is effectively replaced by or constructed from a user’s publicly available identity information (e.g. name, email address, IP address, etc.) which uniquely identifies the user and can be undeniably associated with the user. The service of a trusted third party called Private Key Generator (PKG) is needed solely to generate private key for users using its master secret key after having authenticated the users. This eliminates the need of CA as there is no need to issue and store the digital certificates.
The main difference between ID-based cryptography and the conventional PKI system using certificates is in the binding between the public and private keys and the means of those keys. Some potential applications of ID-based cryptography in particular encryption include access control, building of encrypted and searchable audit log, and keyword search. However, key escrow or key recovery problem is inherent in ID-based cryptography due to the dependence on the PKG and this somehow limits its usage to closed group applications. Key escrow may be desirable in circumstances where an audit trail is required, for instance, in resolving disputes or in monitoring employee activities.

Prof. Dr. Heng Swee Huay is currently a Professor at the Faculty of Information Science and Technology, Multimedia University, and the Director of Research Institute for Digital Security. She received her Doctor of Engineering degree from the Tokyo Institute of Technology, Japan; and both her B.Sc. (Hons) and M.Sc. degrees were from Universiti Putra Malaysia. She has about 20 years of research experience in the areas of Cryptography and Information Security.

