Biometric Authentication: what is biometrics? why is biometrics? How is biometrics?
In 2018, Spiceworks, a marketplace that connects the IT industry for helping technology personnel in the technology domain, conducted a survey about the adoption and security of biometric authentication technology in the workplace. The survey study revealed that there is 62% of organizations employing biometric authentication technology, and it was predicted that closely 90% of businesses will adopt such authentication technology by year 2020. The findings signify the popularity and potential of biometric authentication technology.
What is biometrics?
The term “biometrics” is originated from the Greek words of “bio” meaning LIFE and “metric” meaning TO MEASURE. Biometrics is a statistical measurement analysis of human’s unique physical and behavioral attributes. In other words, a person is authenticated or identified based on his or her physical or/and behavioral traits. Physical traits include but not limited to face, fingerprints, palmprints, finger geometry, iris, retina, vein and etc. On the other hand, behavioral identifiers are voice, gait, hand gesture, keystroke patterns and recently we have touch-stroke patterns due to the wide-spread of smartphone usage.

Example of physical identifier: Face data (photo source: https://www.bbc.com/news/technology-48222017)

Example of behavioral identifier: voice signal (photo source: https://www.hindipanda.com/speech-recognition-technology/)
Why is biometrics?
How is biometrics?
Perhaps, to be precise, what are the trends of biometrics authentication technology nowadays?
Hackers are finding ways to undermine the reliability of biometrics technology. Therefore, besides improving the accuracy performance of biometrics authentication, developers are also working hard for designing and developing a robust biometric authentication system against “presentation attacks” such as spoofing. Liveness detection is an alternative to detect a spoof attempt. Through liveness detection, the biometric source can be identified as a live human or a fake representation. For example, in face recognition, the subject is required to smile or say “O” while performing authentication.
From the Fintech Malaysia 2018 report, there are more than RM6.5 Trillions online transactions, including online banking, credit card transaction, debit card transaction, E-money and mobile banking. As security concerns, we hope to catch problems before fraud transactions happen. Hence, continuous authentication is desired, especially in the online financial transactions. Continuous authentication algorithm will periodically verify the user to ensure the security of the transaction beyond the entry point. How the user behaves (via keystroke patterns, touch-stroke patterns etc.), geolocation information or any personal information that the user enters will be considered as the measurement scores.
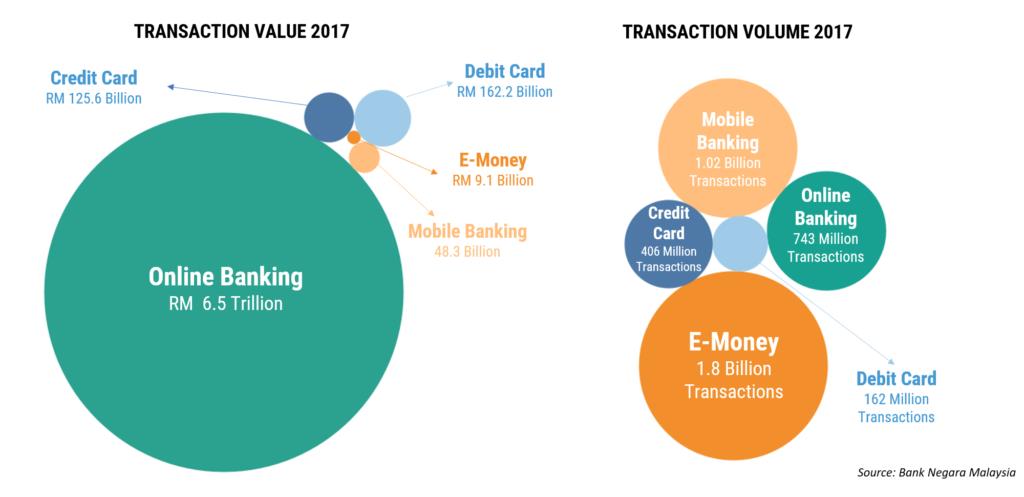
Fintech Malaysia 2018 report. (figure source: https://fintechnews.my/17922/editors-pick/fintech-malaysia-report-2018/)

Dr. Pang Ying Han is currently an Associate Professor at the Faculty of Information Science and Technology, Multimedia University, and a full member of Research Institute for Digital Security as well as the chairperson of faculty research centre- Centre for Ubiquitous Computing and Communication (CUCC). She received her PhD, M.Sc. and B. Eng Electronics (Hons) degrees from Multimedia University, Malaysia. She has about 16 years of research experience in the areas of Biometrics, Security Technology and Pattern Recognition.

